When Reliability Matters

QNX Accelerate
Develop QNX Neutrino RTOS 7.1-based products in the cloud
Build mission-critical embedded systems based on BlackBerry® QNX® technology with QNX® Accelerate. By harnessing the agility, speed, and scale of the cloud, this initiative empowers developers in new ways—enabling better collaboration, increasing development efficiencies, and reducing time-to-market.
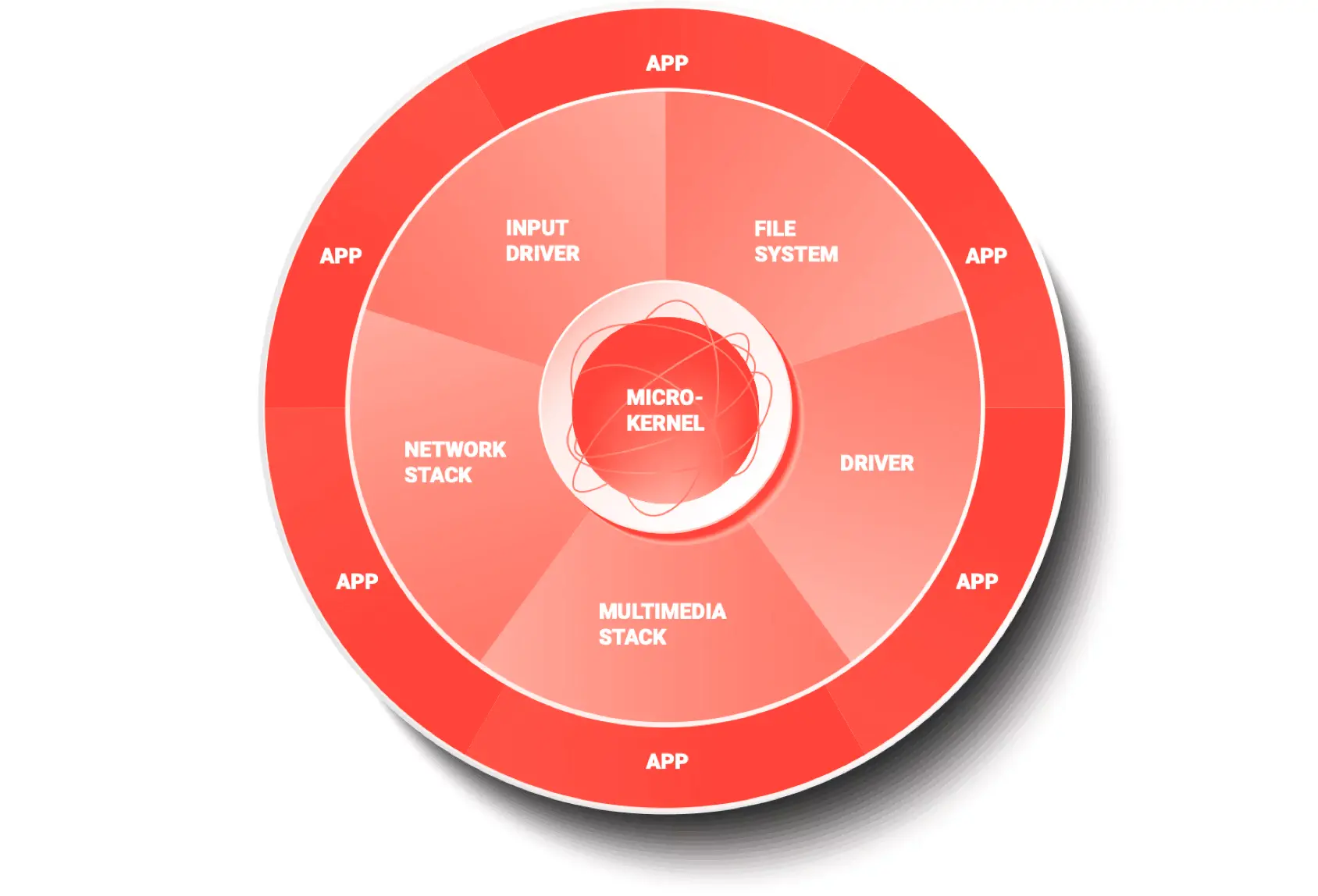
Microkernel Reliability
The QNX Neutrino RTOS microkernel isolates every application, driver, protocol stack and filesystem in its own address space outside the kernel. A failed component won’t take down other components or the kernel; it can be restarted immediately, with minimal impact on performance.
- Add new hardware or drivers, confident a driver failure won’t result in a system failure.
- A high-availability manager can perform multistage recovery when services or processes fail.
- Our architecture enabled us to safety-certify QNX® OS for Safety, so you can focus on what you build—not the OS you built it on.
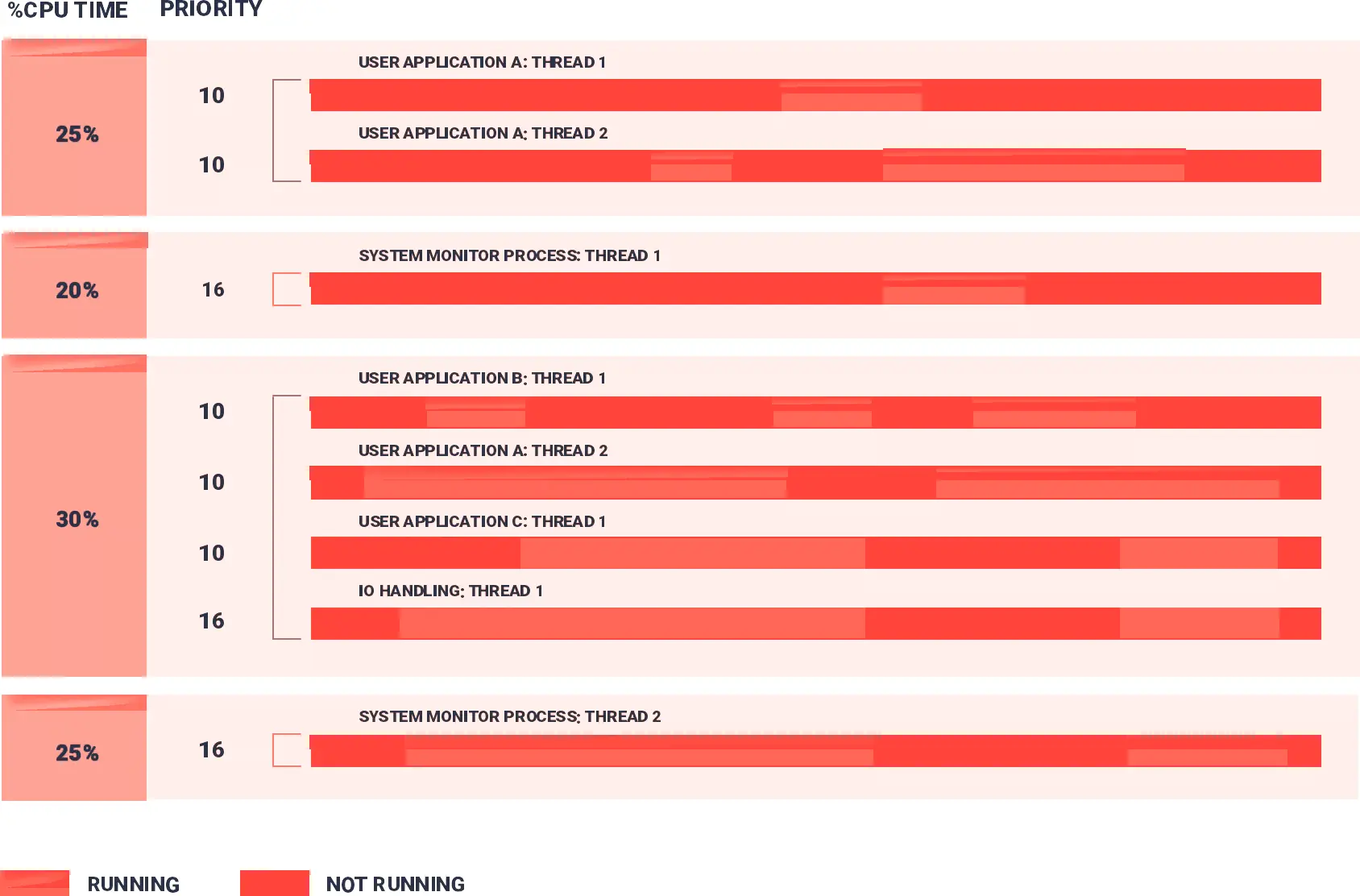
Real-Time Availability
System resources are available when needed and tasks complete when they are supposed to.
Designed to scale on the newest ARM and x86 multicore systems on a chip (SoCs), the QNX Neutrino RTOS supports asymmetric multiprocessing and symmetric multiprocessing (SMP), as well as bound multiprocessing, a QNX improvement on standard SMP.
Our adaptive partitioning enables critical processes to get the CPU cycles they need. You configure time partitions, so that processes that need additional power can access unused cycles from other processes’ budgets.

Comprehensive, Layered Security
Easily configure security profiles with the granularity you need for your systems, as well as monitor and audit their integrity.
The QNX Neutrino RTOS’s comprehensive, layered approach to security allows you to implement exactly the security protocols you need to mitigate threats and harden your systems:
- Granular control of system privilege levels; encrypted and self-verifying filesystems. Implementing AES 256 encryption and lockable encryption domains.
- Secure logging of system activities.
- Heap, stack and memory protection.
- Secure boot implementing TPM and TrustZone.
Learn more about the QNX Neutrino RTOS 7.1.
Related Products and Services





