Imagine you’re that architect building your dream home. Every decision – the layout, the materials, the placement of walls and doors – is a deliberate choice to protect what’s valuable inside. You see the whole system – the framework, the access points, the potential vulnerabilities. It’s not just about walls and windows; it’s about understanding where weaknesses might exist and how to secure them. Is there a crack that could widen under pressure? A door that could be pried open? A window that could shatter? Identifying those vulnerable points is just as important as reinforcing them.
In the digital world, the product you build is your home. And just like a physical house, every component needs to be built with intention, with an unwavering commitment to security. The European Union’s Cyber Resilience Act (CRA) (Regulation (EU) 2024/2847) serves as the blueprint, ensuring that every digital product entering the EU market is constructed to endure. It’s about using the best materials, hiring the right experts, and ensuring that when the storms hit, your digital home doesn’t just stand – it holds firm.
Think of the EU CRA as your building code – a framework that guides you, the architect, as you construct your digital home. Every choice you make, whether it’s using open-source components, commercial off-the-shelf software, or custom-built solutions, must align with this blueprint. It’s not just about compliance; it’s about ensuring that every door is reinforced, every window is shatterproof, and every foundation is solid. Because when the digital storms hit – and they will – it’s the strength of those choices that determines whether your product stands tall or crumbles under pressure.
What the EU CRA Protects
The EU CRA serves as a critical regulatory framework to bolster the cybersecurity of digital products across the European Union. It addresses the increasing proliferation of connected devices and the corresponding rise in cyberattacks that threaten user safety, data privacy, and market stability. By enforcing a uniform set of cybersecurity requirements, the CRA protects consumers and businesses from the financial, operational, and reputational damages caused by vulnerabilities in digital products. It also seeks to eliminate the legislative patchwork across EU member states, fostering a more cohesive and secure digital ecosystem. Ultimately, the CRA’s objective is to mitigate cybersecurity risks associated with both hardware and software products, ensuring they remain secure throughout their entire lifecycle.
Think of the EU CRA as the unified foundation that holds your digital home steady. It entered into force on December 11, 2024, setting a series of deadlines that manufacturers must adhere to. By September 11, 2026, all manufacturers must comply with vulnerability reporting obligations – the act of identifying cracks in the digital structure before they splinter into something more dangerous; and the full compliance window closes on December 11, 2027.
While the CRA introduces broad obligations for digital products, its application is more nuanced than it may first appear. Not every product falls under its regulatory roof, but digital components, such as embedded operating systems and connected services, are indeed within scope, especially when they are part of commercial offerings. The CRA excludes a subset of products within certain industries that fall within the purview of other cybersecurity regulations:
- Medical Devices: These are regulated under the EU Medical Devices Regulation (MDR), which already includes cybersecurity requirements to ensure patient safety and system reliability during critical moments.
- Defense and National Security Products: Exempt from the CRA due to their classification under national and EU-level defense frameworks designed to prevent adversarial exploitation.
- Automotive and Aviation Sectors: Governed by their own cybersecurity standards (e.g., UNECE WP.29 for vehicles), which address the unique risk profiles of these industries.
- Open-Source Software: Purely non-commercial open-source software is exempt. However, once it becomes part of a commercial product, it falls under the CRA’s regulatory scope.
Blueprint of Potential Vulnerability Points
The CRA outlines several critical vulnerability points within digital products that manufacturers must address to comply with the regulation:
- Supply Chain Security: Software components, including open-source software, pose risks when sourced from unverified or inadequately secured suppliers. A comprehensive Software Bill of Materials (SBOM) is required to track and manage these components effectively.
- Update and Patch Management: Unpatched software can serve as a gateway for attackers. The CRA mandates that manufacturers implement security updates and notify users when support periods end.
- Remote Data Processing: Digital products relying on cloud or external data processing solutions are particularly susceptible to cyberattacks. The CRA includes requirements for securing these data flows against unauthorized access.
- Authentication and Access Controls: Weak authentication mechanisms can allow malicious actors to gain unauthorized access. The CRA specifies robust identity verification and access control requirements.
- Configuration and Setup Processes: Initial device configuration is a common attack vector. The CRA emphasizes secure-by-default settings to prevent exploitation of poorly configured devices.
- Product Modifications and Updates: Unauthorized or poorly executed updates can introduce new vulnerabilities. The CRA defines substantial modifications and requires reassessment of cybersecurity post-modification.
Foundations for Ensuring a Secure Device
To meet the CRA’s cybersecurity requirements, particularly those outlined in Annex I, Part 1 and 2, manufacturers must embed security into every stage of a product’s lifecycle:
- Secure Development Lifecycle (SDLC): Implement secure coding practices and conduct vulnerability testing throughout development. Regularly update risk assessments to address emerging threats.
- Comprehensive Vulnerability Management: Develop a structured vulnerability management process, including detection, notification, and remediation of security flaws. Maintain a vulnerability disclosure policy.
- Transparency and Documentation: Provide users with clear and accessible documentation about cybersecurity measures, including the duration of security update support and identified vulnerabilities.
- Security Updates: Establish robust update mechanisms that can deploy security patches without disrupting device functionality. Ensure that updates are separated from feature upgrades to minimize risks.
- Incident Response Plans: Prepare and maintain a cybersecurity incident response plan, including procedures for notifying users and regulatory bodies in case of a security breach.
- Risk-Based Approach to Compliance: Classify products based on their potential impact and apply proportionate security measures. High-risk products must undergo stricter conformity assessments and third-party verification.
How the QNX Software Ecosystem Helps with Compliance
As the architect of your digital product, you hold the EU CRA blueprint – and with it, the responsibility to think about compliance not as an afterthought, but as an integral part of the design. It’s not like you would construct a house and then ask if it meets code; you’d bake those requirements into every decision, from the layout of the rooms to the placement of doors in the house. The same applies to cybersecurity. Compliance with legislation needs to be woven into the very fabric of development, guiding choices around components, configurations, and controls. Because just like a safe home, a secure product doesn’t begin with the final coat of paint – it starts with the foundation.
Much like building codes that guide architects through proven best practices for safety and resilience, IEC 62443 offers a framework for securing industrial automation and control systems at an organizational rather than product level. For you, it means aligning with a standard that could provide some level of clarity and consistency in meeting CRA obligations. While the EU hasn’t officially designated it as the default path to compliance, there is a push for harmonization.
For architects looking to build on a solid foundation, software components certified to ISO/SAE21434, a cybersecurity standard tailored specifically for road vehicles, are worth consideration. It’s a standard considered more stringent than many general-purpose cybersecurity frameworks, and like the EU CRA, it requires a deep lifecycle-wide approach to cybersecurity: from risk assessments during the concept phase, through secure design and implementation, to post-production monitoring and incident response. Certification to this level means that you don’t just meet the baseline requirements – it details that your organization adheres to rigorous processes and has the documentation needed for certification. Using products like QNX that are certified to this standard is like choosing reinforced steel over plywood.
With QNX, security isn’t considered a feature – it’s a foundational philosophy. We take a layered approach that starts at the silicon level, working closely with hardware partners to ensure a trusted base, and extends through our collaboration with ecosystem software providers to deliver secure, reliable integrations. All our products are built around the microkernel architecture with added services to help you manage security throughout the software development lifecycle. From design to deployment, the QNX portfolio provides the tools, guidance, and infrastructure to help you build systems that are resilient by design. The approach to cybersecurity is made simple using a layered defensive strategy, much like the layers of an onion, where each ring represents a critical barrier designed to protect the integrity of the system. At the very core lies the trusted hardware, the immutable root of trust that everything else is built upon. Moving outward, ECU authentication ensures each component is uniquely verified through secure manufacturing, acting like a digital fingerprint. From there, tamper protection defends against unauthorized changes with encrypted file systems and a trusted disk.
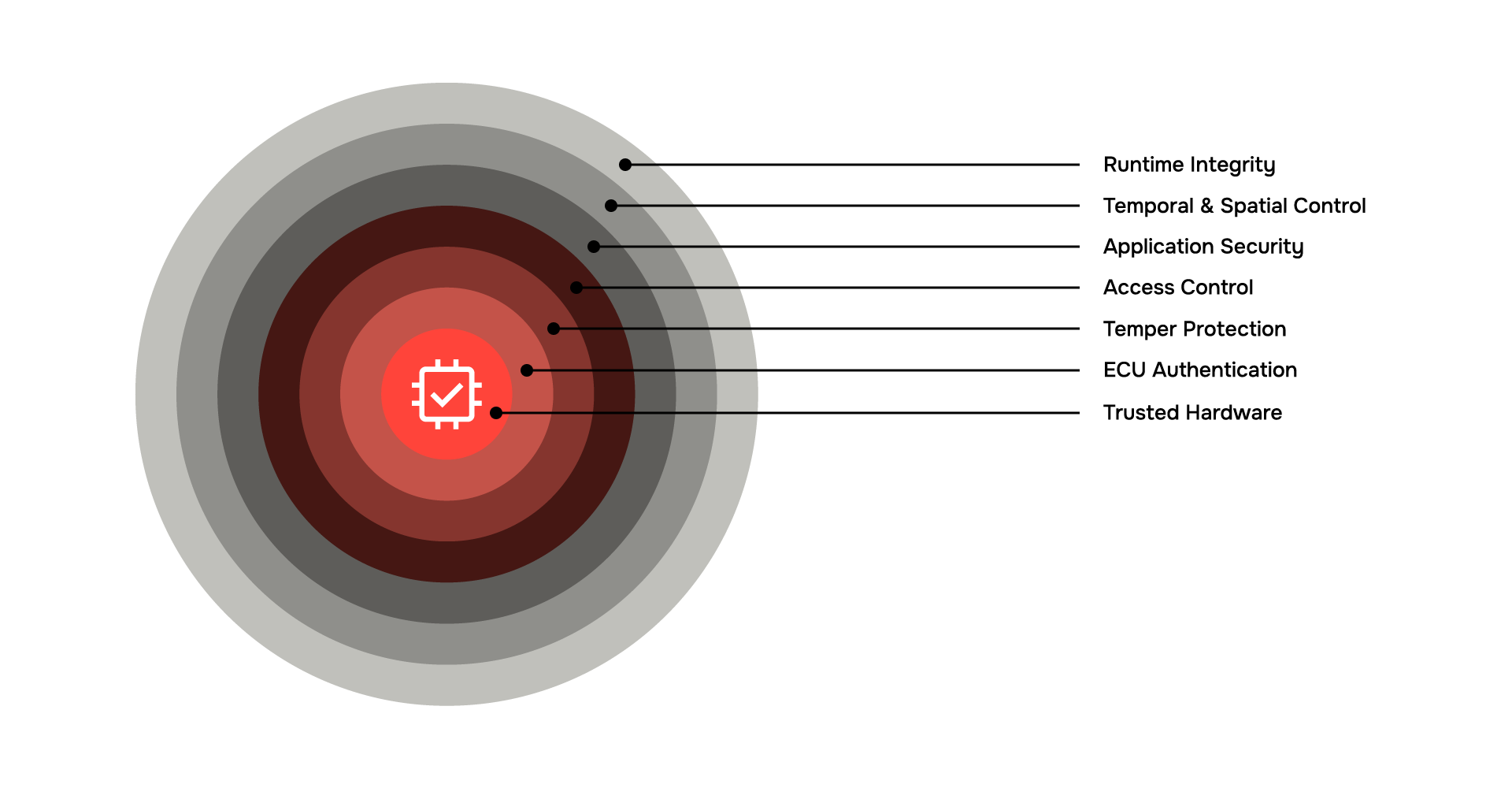
QNX Trusted Disk ensures that file system contents are encrypted and verified at runtime, protecting data from unauthorized access and tampering. Combined with secure boot, it creates a trusted execution environment where only validated, unmodified software is allowed to run.
Access control defines strict policies and permissions, supported by the QNX microkernel’s capabilities like discretionary access, process isolation, and memory management.
QNX supports Mandatory Access Control, enabling system-enforced policies that strictly govern how processes interact with files, resources, and other processes. This ensures that even if an application is compromised, it can’t exceed its predefined boundaries, locking down potential attack paths at the policy level.
Next, application security protects against unauthorized code execution using fortified functions and tools like Pathtrust, while temporal and spatial control enforces safe CPU usage through adaptive partitioning, keeping rogue processes in check.
QNX toolchains support modern exploit mitigation technologies such as Address Space Layout Randomization (ASLR) and Relocation Read-Only (RELRO). These hardening features make it more difficult for attackers to predict memory layouts or overwrite critical function pointers, adding another layer of protection to applications running on the system.
Finally, the outermost layer, runtime integrity, continuously monitors system behaviors for anomalies, ensuring that even if an attacker breaks through, their actions can be detected and neutralized. Each of these layers works together to form a resilient, defense-in-depth approach that helps you secure your systems from the inside out.
Security isn’t just about how strong your walls are today – it’s about how well they hold up over time. Many embedded systems are built to last for a decade or more, which is why the QNX long lifecycle support is quintessential to compliance with the EU CRA. But longevity without vigilance creates risk. With extended support services options, including creating Software Bill of Materials (SBOMs) and continuous monitoring for Common Vulnerability and Exposures (CVEs), QNX services provide timely guidance and documentation to mitigate emerging threats.
While QNX provides a strong foundation for cybersecurity, the EU CRA introduces requirements that extend beyond the core product and services offering, such as Secure Boot, which requires hardware-specific TPM drivers, and an end-to-end Over-the-Air (OTA) update solution. To address them, QNX works through a trusted partner network, collaborating with security solution providers to help you build a complete, end-to-end CRA-aligned solution. In the end, it’s not just about securing the platform – It’s about building a full story of resilience, documentation, and responsiveness.
Departing Thoughts
The Cyber Resilience Act is transforming how digital products are secured, maintained, and certified. As the architect, taking a proactive approach to compliance will not only meet EU regulatory standards but will also gain a competitive advantage by delivering products that consumers and businesses can trust.
With QNX and our partner ecosystem, you can fortify your digital products, simplify compliance, and enhance security from design to deployment.
Is your product CRA-ready? If not, contact QNX to know more about how we can help you with compliance and build a secure future in the EU market.
